Shifting Security Left: The Innovation of DevSecOps – Security Boulevard
What is DevSecOps? It involves taking all the practices of DevOps and pulling in security practices to improve security. Tom Stiehm (@thomasstiehm) explains the process.
In DevSecOps, we want to shift security left. Shifting left brings security into the application process earlier instead of allowing it to be an afterthought.
Why Shift Security Left?
Shifting left lets us deal with security issues early and often. If we leave security practices to the end, we end up with security defects in production. So shifting left reduces risk and the costs of fixing security problems.
As with other bugs, finding and fixing security bugs earlier leads to fewer errors and fewer compromises.
How Can We Do This?
Let’s next talk about how we can shift security left.
We start with proactive processes instead of reactive processes. Then we architect and design security early. Finally, we automate testing that focuses on security as well.
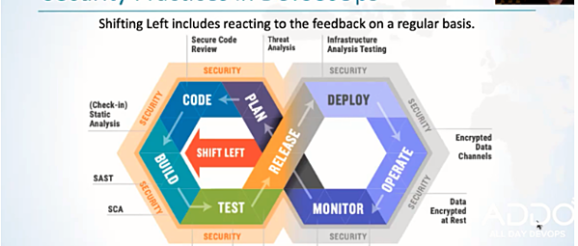
Security practice in DevSecOps from Tom Stiehm’s “Shifting Security Left: The Innovation of DevSecOps” presentation.
An important step is to also review the automated test results and remediate early. Without that step, we won’t be fixing problems before they hit production.
SCA and SAST
When looking at the model above, look at all the ways that you can bring security into every step. When planning, we can use threat analysis to figure out what our risks for the application are. Then when we write our code, we can use static analysis (SCA or SAST) to make sure we’re not introducing vulnerabilities like SQL injection. With SAST, we’re analyzing the code we’ve written for common vulnerabilities. On the other hand, with SCA, we’re looking for vulnerabilities in our dependencies like open-source libraries. The combination of SAST and SCA will help us determine if we have something that (Read more…)
